Original Research
Locks & LeaksRisk, resilience, and red teams! Promoting and supporting the Physical Red Teaming profession, along with articles, tutorials, and stories about physical security, red teaming, and security risk management.
[Resources] Threat Assessment Graphics
Lengthy written reports rarely relay risks effectively.
Visuals are memorable, while reports are arduous and easily forgotten. Whether you are a consultant, a risk assessor, or an internal red team, the ability to effectively communicate your top threats is essential to making a material difference with your work and findings.

Threat Assessment
Depending on the audience, various threat taxonomies are useful for threat assessments. Leaders care about who is targeting them and the organization they are tasked to protect and how they are being targeted. Intelligence teams care about threat actor motivations and capabilities. Threat actors (who) and threat vectors (how) provide valuable information, but they often lead to a common security fallacy: the Actor-Centric Fallacy.
Reporting
As you create visuals and graphics for your threat assessment, risk assessments, or red team reports, there are complicated and interrelated factors that need to be examined. To visualize these concepts and create clear and compelling cases for leadership to act, it is necessary to produce simple graphics, but also have ample research, matrices, intelligence, and research to support your positions. These may include deep dives into known variables such as:
-
Threat Actor: Who will target your organization?
-
Motivations: Why will they target you?
-
Capabilities
-
Known: What do we know this adversary is capable of?
-
Suspected: What do we suspect them to be capable of?
-
-
-
Tactics, Techniques, and Procedures (TTPs): How will they target you?
-
This is sometimes referred to as “Threat Vectors” as well.
-
-
Threat Surface: What in your organization will be targeted by this threat actor?
Threat Modeling
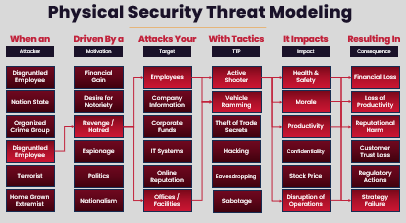
For red teams, we encourage a simplistic approach to physical threat modeling. Once you select an adversary to emulate, determine the scenario that will be tested and identify what the expected consequences may be.
What do Blue Teams Defend Against
The broader security organization is referred to as the blue team, while a red team is the fake adversary that tests the blue team environment (to sometimes test efficacy of a particular control, and sometimes to determine a holistic security picture of the entire organization) and helps them improve. To overly simplify and summarize the role of the blue team, they must triage a million threats, vulnerabilities, assets, and risks and successfully implement strategies to address the most significant ones. From a threat perspective, which of the following will be the easiest for the security team to come up with a strategy to address:
-
The threat of international terrorism, or
-
The threat of an IED being placed in the building lobby?
In this oversimplified scenario, a terrorist is who will attack, and an Improvised Explosive Device (IED) in the lobby is how someone could attack the organization. The terrorist is the Threat Actor, while the IED in the lobby is the TTP. As a security professional, it’s far easier to develop a strategy to mitigate TTPs than it is to mitigate a complete modus operandi for a particular threat actor. Terrorists, nation states, and competitors each have 20+ TTPs they often use to achieve their goals.
Whereas there are research-driven means to narrow these TTPs even further, and we will write more on threat modeling, actionable intelligence for red teams, and threat intelligence in general, doing it effectively typically requires a considerable resource allocation.
Effective Visuals for Reporting
Good visuals and illustrations bring a red team report to life. Your reports and presentation should have graphics that give color to the following areas:
-
Who: Who did you select to emulate for this assessment
-
Why: Why were they selected
-
TTPs: What TTPs were selected
-
Outcomes: What were the outcomes of the tests
Only one of the four areas that typically require graphics are about the outcome of the tests. While identifying how security performs is the ultimate purpose of a red team test, it’s not the purpose of a red team. A red team is part of the blue team, in disguise. Ultimately the success of a red team relies on changes being made by the blue team in response to your findings. For that to happen, you need blue team buy-in as to what you were testing, and how you tested it. If you tell a compelling story, build a relevant narrative, and provide framing and context around the tests you conducted, you are more likely to succeed in remediating the identified vulnerabilities and fortifying the organization you work for or partnered with.
Risk Assessment & Red Team Templates
While we’re both adamant supporters of the open-source community and philosophy, we are also big supporters of being able to pay rent and buy groceries. For those interested, we have made some of our internally developed infographics, visuals, and report templates available for our paid subscribers. If you represent a non-profit or a school, please drop us a line and we’ll send you what you need for free. If you are interested in subscribing, please click below to do so and you’ll get access to our template library, paid-only posts, and other cool benefits. You can also request specific templates or graphics from us, or request that we cover specific topics around red teaming that you’re struggling with. Thanks for reading!
Paid users – keep scrolling for access to our risk and threat assessment resources. Threat Modeling templates, graphics, and more will be out the third week of April.
PowerPoint Templates
-
[Redacted – Available to Clients and Locks & Leaks Subscribers]
-
Includes: Threat Actors
-
Includes: Tactics, Techniques, and Procedures (TTPs)
-
