Original Research
Locks & LeaksRisk, resilience, and red teams! Promoting and supporting the Physical Red Teaming profession, along with articles, tutorials, and stories about physical security, red teaming, and security risk management.
reaking Into Red Teaming – Phase 2
This is the third post in a four-part series: Breaking into Physical Red Teaming. If you haven’t read Phase 1, it contains a description of timelines, an overview of our approach, and details on how we are working to prepare the next generation of physical red teamers. You’re a red teamer so we know you like breaking the rules, but we suggest you start at the beginning for this one.
Timeline
This post focuses on the technical skills you should have as a physical red teamer. Phase 2 (steps 4 – 8) should take three months for you to complete. If you find yourself finishing early, we suggest that you do not proceed to Phase 3. Instead, find your favorite hands-on skill or an area you haven’t explored yet, and focus on that. Learn broader or deeper as it relates to hands-on red teaming skills. Boredom breeds creativity, and creativity is a red teamer’s best weapon. Practice honing your creativity in your free time. As a red teamer, it’s your most valuable intangible skill.
Step 4: Lockpicking
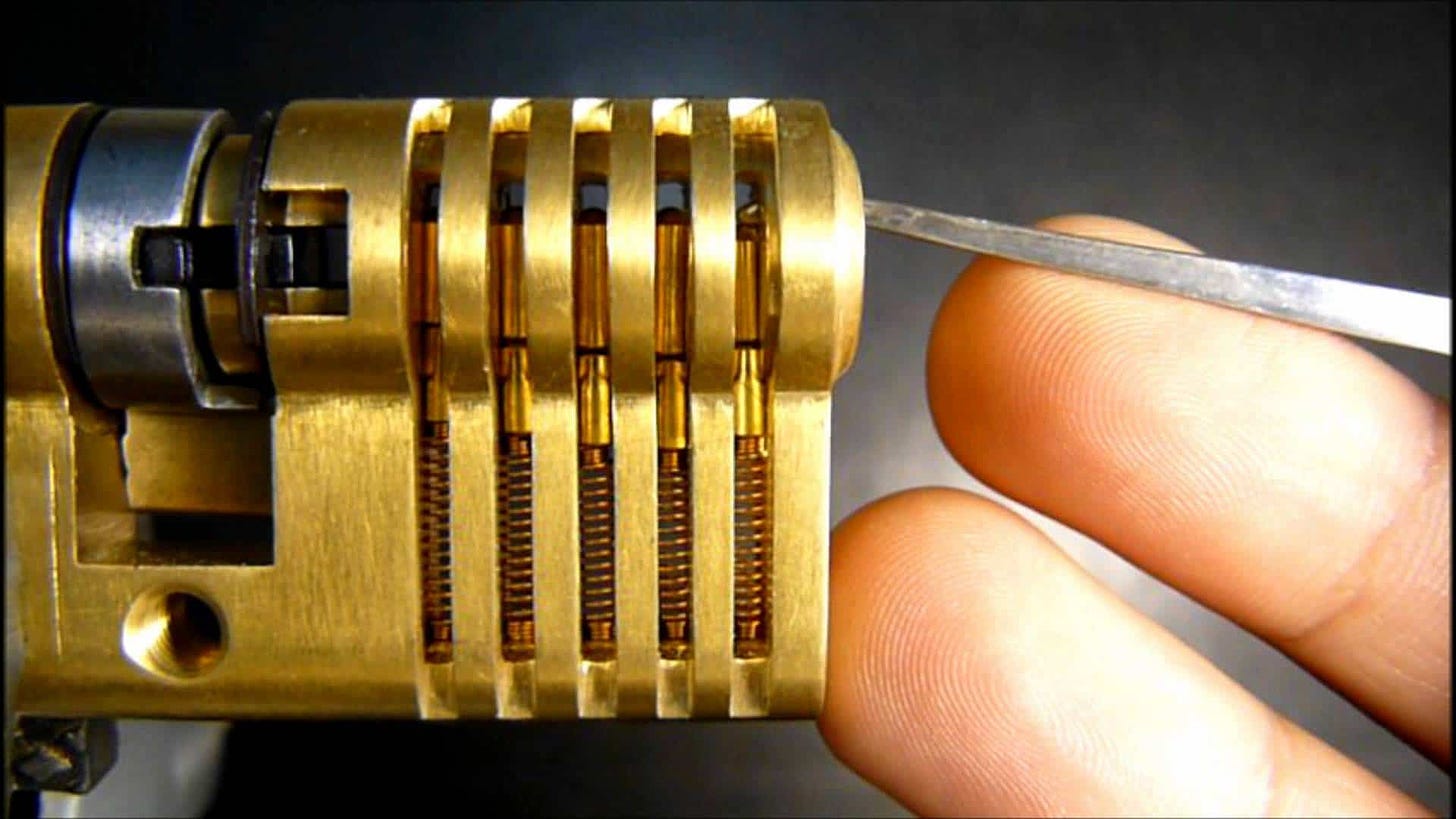
Become proficient at lockpicking. You don’t need to be an expert but aim to be intermediate. The skill itself will come in handy from time to time, but the real benefit comes in the fringes. By virtue of joining the lock picking community, you will find resources, perspectives, and industry voices that will shape you as a professional. There are many ways to pursue lockpicking as a hobby and a career skill. I suggest you pick any two from the following list:
-
Reddit/lockpicking: Try to make it to a greenbelt or beyond!
-
Follow the Lockpicking Lawyer and watch at least 20 videos
-
Take the Covert Methods of Entry (CMoE) Course (This is an expensive course – I recommend only doing it if your employer pays for it, or if you can easily afford it)
-
New (Jan 2024) Locksport Book
-
Get and complete one of these practice sets:
-
Advanced Option: Note you are probably ready to progress after you complete Lock 5. If you complete Lock 6 that is a bonus.
Step 5: Social Engineering
Social engineering is a complex, controversial topic in the security awareness, penetration testing, and ethics spaces. It is also one of the essential skills for red teamers. You don’t need to be extroverted or even good with people in order to become an effective social engineer. The most important thing is to know yourself, have self-awareness into how others see you, and exploit that to your advantage. For example, if you’re a boisterous Type A, you can walk up and dive into an energetic conversation with security officers and they may forget to ask you how you even got into the building. If you are quieter, anxious, or timid, then find a social engineering role where you can use who you are to your advantage. For example, maybe you had an interview with the CEO and your wallet fell out of your pocket, but you can’t email the CEO for fear of not getting the job. You also can’t explain where it is exactly but can show the security officer. If you’re nervous about social engineering, or interacting with people in general, then the security officer will see that….which is good. You told them a story where it makes sense that you feel nervous about asking. Your nervousness just went from being a weakness to an essential part of your story. Know yourself, and use that knowledge to your advantage.
If you are bad at lying, we have good news for you! The best lies to tell during social engineering are those closest to the truth. Often you can tell your target nearly the entire truth about where you need to get into, how your boss will be angry if you don’t succeed, that you’re new to the job, etc. All of these may be true, you just switched from being a red teamer to a janitor, but all the peripheral cover story data may still be true. Becoming an effective social engineer is intimidating for many; however, most people thrive in these roles once given the opportunity and a little bit of practice. To learn both theories and tactics, start by reading a primer (IBM, Wikipedia, or article of your choice), watch a nice 2-minute example of effective social engineering, and then do two of the following:
-
Read a book from renowned hacker Kevin Mitnick. My favorite is The Art of Deception.
-
Consider a book from Christopher Hadnagy:
-
Human Hacking: The Art of Social Engineering
-
Human Hacking: Win Friends & Influence People
-
NOTE: There are currently allegations against Hadnagy relating to his violation of the DEF CON conference code of conduct. You can read more about it yourself. I want readers aware of allegations and able to make their own decision.
-
-
Attend Social Engineering (SE) Village at DEF CON: This is the single best educational experience you can have on your path to learning SE. You will watch live as individuals and groups conduct SE phone calls all over the country, and if you choose, you can participate and enter the booth to try it yourself.
-
Watch one of the following Videos
-
For an academic and economic view of Social Engineering, read ENISA’s 2023 Threat Landscape Report. The introduction and overview are excellent, and the SE-specific section starts on page 71.
-
Follow two of my favorite voices on Social Engineering and read several articles and/or watch their videos:
Bonus: I have heard Maxie Reynold’s book The Art of the Attack is quite good, but have not read it myself. If you do, please let me know how you liked it, and whether you felt it prepared you for a career in physical red teaming.
Step 6. OSINT
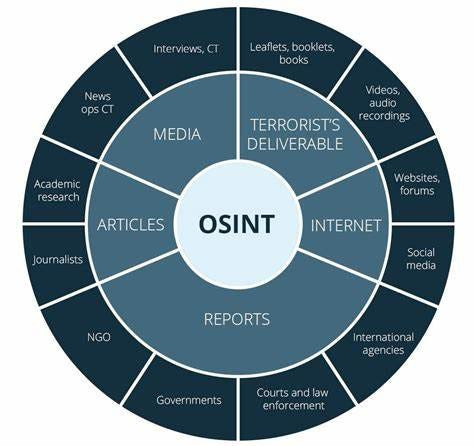
Open-Source Intelligence (OSINT) has bloomed into a standalone profession in recent years, and the skills involved are relevant to nearly every cyber, physical, or information security professional. The knowledge of what information is generally and publicly available, and ability to find it, are a skill that can set you apart. OSINT has sprung into the mainstream over the past decade and moved from a skill many analysts had to a standalone profession with academic courses, schools, companies, and professionals all dedicated to only OSINT. In many ways, Locks & Leaks is using OSINT’s professional emergence as a roadmap to learn from as we promote physical red teaming as a standalone profession.
To gain OSINT skills of a physical red teamer, we recommend to:
DO THIS: Michael Bazzell is a household name for OSINT. He has the original, and best, books around OSINT and privacy. I highly recommend getting his latest book from 2023, reading it in full, and practicing with the tools and resources he covers. Do this, and you will be ahead of 90% of security and even many OSINT professionals.
DO TWO OF THESE:
-
Spend a few hours clicking through, researching, and bookmarking key resources from SANS guide on getting into OSINT. Note the age of some of the recommendations. Anything that has not been updated in two or more years is likely out of date. You can do this on SANS’ website, or any of the below guides:
-
Job-focused starter’s guide to OSINT: OSINT-Jobs
-
The first and best to institutionalize OSINT: Bellingcat’s Guide
-
Resources for practioners that want to go deeper: The Sleuth Sheet
-
If you want to build your street cred with OSINT, here are great recommendations: Secjuice
-
Consider a GOSI Certification.
-
Become familiar with the OSINT Framework.
-
-
Read Rae Baker’s Book: Deep Dive – Exploring the Real-world Value of Open Source Intelligence
-
Get involved in an OSINT Capture The Flag (CTF) Community, Team, or Group. Solve a few CTFs, get stumped, learn new skills, and try again. Here are some great resources:
Step 7: PACS Attacks

Physical Access Control Systems (PACS) are the badges, badge readers, door control panels, badging software, and other hardware and software involved in access control. There are many attacks on these types of physical security systems, and as a physical red teamer, you will be expected to be knowledgeable about them. The primary attack types you should know about:
-
Man-in-the-Middle: ESPKeys are the best example of this. This is a type of eavesdropping attack.
-
Credential Cloning: Badge Cloning Attacks
-
DDOS Attacks: Denial of Service for Badge Readers
-
Tampering: Physically manipulating PACS hardware (e.g., shorting a circuit, implanting a device, etc.)
-
Relay Attacks: Involve capturing the signal from a legitimate access device (like a key fob or card) and transmitting it to the reader from a distance, effectively tricking the system into thinking the attacker is the legitimate user. This type of attack is particularly effective against systems that do not employ proper distance bounding protocols.
-
Side Channel Attack: Although rare, it’s not out of the picture when it comes to hacking PACS.
There are occasionally excellent conference talks (con talks) about these types of attacks, but they have become rarer as PACS companies become aggressive in targeting researchers who publicize their vulnerabilities. A few of my recommendations:
-
Watch One of these Two con talks by Babak Javadi & team.
-
Follow Babak on LinkedIn
-
-
Take some time to research this yourself; there are a slew of resources out there focusing on many technologies, vendors, card types, and protocols involved in physical access control systems.
Step 8: Bypass Techniques

Here’s the fun one! Bypass techniques offer a range of ways to circumvent security measures – typically doors and latches. Most physical red teamers should be proficient at all of these, good at 50%, and great at 25%. Having a team with diverse skills to tackle whatever measures you face will be important. Become comfortable with how these tools feel in your hand when attacking different locks, doors, and latches. Watch videos, set Google Alerts, and keep an eye on the latest exploits and add-ons when it comes to the ever-expanding market of bypass techniques. Here are some of the most common:
-
Under the Door Tool (click the “Video” tab to see it in use)
-
Locks/Keys (see Step 4 above)
-
Picking
-
Bumping
-
Impressioning
-
Decoding
-
-
Shims (Video | Cylinder Shim | Steel Shim)
-
Request to Exit (REX) Trigger (Whisky | Compressed Air | Hand Warmer | Tools)
-
Elevator Hacking (Video)
-
Many More: Find videos of your favorite bypass techniques on YouTube and follow their channels. Find those presenting new exploits at cons and follow their social media or set up Google Alerts for them. In general, red teamers will be expected to stay appraised on the latest and greatest in these techniques.
-
Note: Inevitably in your career you will be stumped during an assessment (or at home practicing) and you will develop a new technique, tool, or both. Share your innovations! Tag your favorite red teamers, present your hacks at conferences, or publish a video/tutorial. The red team industry moves forward by sharing innovation with the community, and the entire security industry moves forward by red teamers pressuring them to improve and fix vulnerabilities before adversaries exploit them.
Conclusion
Don’t let anyone gatekeep red teaming for you. No one is expected to be perfect, or even good, at all of the above techniques. Learn and practice as you go. If you don’t have a job that involves red teaming, build an at-home lab to practice bypass techniques, or practice on various buildings and lock types where you have connections (get permission!). Spend time to get both familiar and adequate at each of the technical skills. Most of red team learning is on the job or in the classroom. If you’re just breaking into the red teaming field, learning the basics of each skillset above should take at least 3 months. I would suggest 6 months if you really want to familiarize yourself, practice, and grow. Whatever timeframe you set for yourself, you now have the context (Phase 1) and the skills (Phase 2) to become a physical red teamer. Now it’s time for the final phase: Employability.
What makes you an attractive, well-rounded red team candidate? What instantly positions you to be a physical red team leader? We’ll discuss the mindset and skills needed in our next post!
If you have questions, thoughts, comments, or insights, please share them below.
