Original Research
Physical Threat Management
Pine Risk Management solves problems, provides answers, assess risk, builds programs, and guides you as you tackle complex, uncertain, dynamic issues.
We offer a customized approach to ensure that you have a clear understanding of your risk landscape and can make evidence-informed decisions to protect what’s important.
Tracking & Modeling Threats
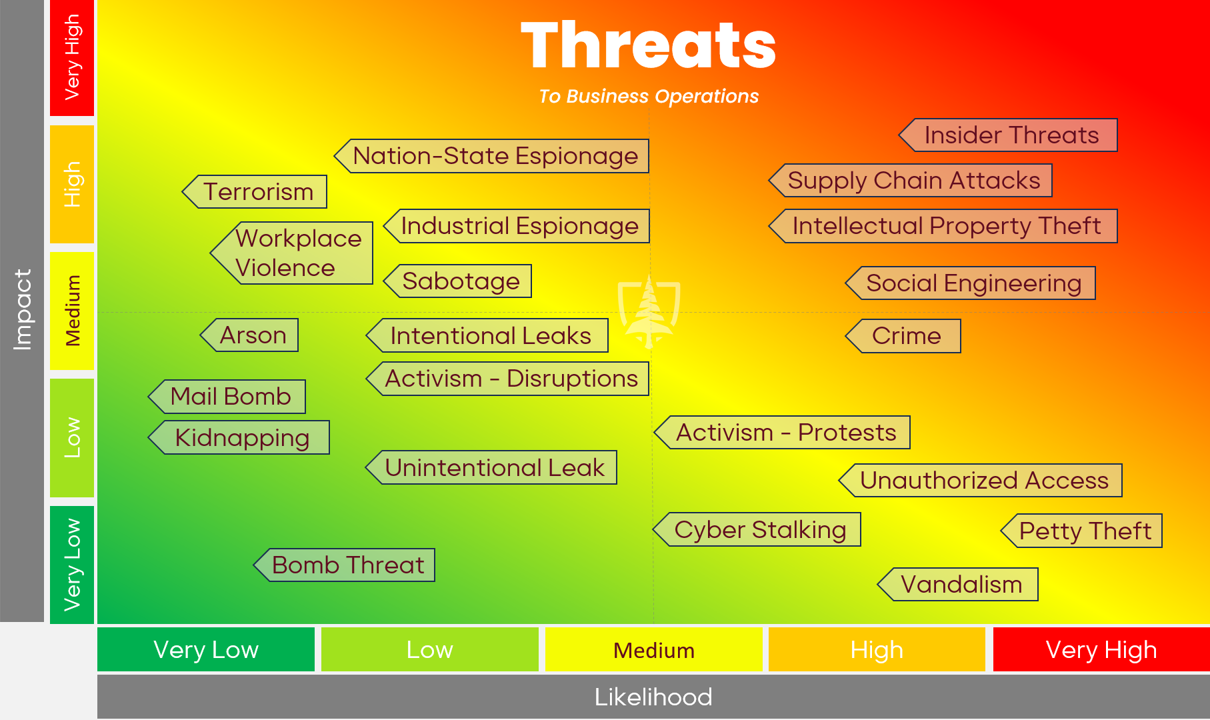
Security is overwhelming. Defenders have to grapple with a wide array of threat actors and the tactics they use. The opinions of experts, business leaders, academics, and politicians about which threats to focus on add to the chaos, making it increasingly difficult to focus efforts and safeguard your organization.
So what is the best route forward? If there was a one-size-fits-all answer it would have been uncovered and published many years ago and whoever figured it out would be rich, famous, or both. Instead, organizations are left with disparate, unorganized, ineffective standards, leading them to jump from one ISO certification to the next CPTED push to major overhauls after an incident happens. It’s ineffective and inefficient, and most importantly it doesn’t provide true security.
At PRM, we don’t think we have that universal answer, but we do have an ideology and a framework that is both customizable and repeatable. The most important recommendation we have as security practitioners and consultants is that you should have a principle, and stick to it. The principles that drive your security decisions should allow you to be open and flexible, while giving you the focus and structure to make quick and logical decisions. We encourage organizations to follow a version of the Pareto Principle (80-20 rule).
For most organizations, we recommend spending 80% of your resources on an all-hazards (or all-risks) approach that develops deep, effective, and mature security capabilities to address a broad spectrum of risks. For the 80%, ignore specific risks and threats, and instead build and mature security controls that can deter, prevent, detect, and respond to many different threats. The remaining 20% is dedicated specifically to those threats in the top right quadrant of your threat assessment.
Sometimes, the opposite is better. Spending 80% of budget on the top 20% of threats. The remaining budget (20%) is spent on an all-hazards approach. This model is best for organizations with top-notch intelligence and risk management teams, who have enough likelihood and impact data to confidently identify their top threats and focus resources on mitigating them. Defense contractors and emerging technology companies with highly valuable intellectual property are best suited for this model.
It is critical to build deep and consistent capabilities that play to your strengths and mitigate your weaknesses. Regardless of your type of business, we work with clients to find the right model, develop a framework, and build a mature and robust security program that mitigates your most significant risks. Most importantly, we build programs that pass tests – both stress tests (red teams) and real-world tests. We’re here to build, test, improve, and validate the country’s best corporate security programs.
